Aarti Shahani
Aarti Shahani is a correspondent for NPR. Based in Silicon Valley, she covers the biggest companies on earth. She is also an author. Her first book, Here We Are: American Dreams, American Nightmares (out Oct. 1, 2019), is about the extreme ups and downs her family encountered as immigrants in the U.S. Before journalism, Shahani was a community organizer in her native New York City, helping prisoners and families facing deportation. Even if it looks like she keeps changing careers, she's always doing the same thing: telling stories that matter.
Shahani has received awards from the Society of Professional Journalists, a regional Edward R. Murrow Award and an Investigative Reporters & Editors Award. Her activism was honored by the Union Square Awards and Legal Aid Society. She received a master's in public policy from Harvard's Kennedy School of Government, with generous support from the University and the Paul & Daisy Soros fellowship. She has a bachelor's degree from the University of Chicago. She is an alumna of A Better Chance, Inc.
Shahani grew up in Flushing, Queens — in one of the most diverse ZIP codes in the country.
-
Brad Smith says governments need to step in and set rules for the Internet giants. "Almost no technology has gone so entirely unregulated, for so long, as digital technology," he says.
-
The top legal officials of 48 states, led by Texas Republican Attorney General Ken Paxton, announced a major investigation into Google's dominance in search and advertising.
-
A theater company in Santa Clara, Calif., has become a place for Indian immigrants working in the tech sector to find a home away from home.
-
At the G7 Summit, President Trump declined to say if he had backed down from his threat to place tariffs on French wine in retaliation for that country's new tax on digital giants.
-
The move in Europe to get tough on tech is partly thanks to an awakening that began with the experiences of women in politics.
-
The El Paso shooter targeted a Latino community and left a manifesto on the website 8chan — hallmarks of a white extremist attack, experts say, and not to be confused with other types of shootings.
-
Regulators missed a chance to find out if deceptive practices at Facebook came from the top when they decided to enter into a settlement with Zuckerberg instead of questioning him, an FTC member says.
-
The FTC and Facebook entered a new settlement over privacy violations. CEO Mark Zuckerberg must give quarterly progress reports directly to regulators. Facebook must also pay a $5 billion fine.
-
Under a settlement with the Federal Trade Commission, the company will pay $5 billion and its co-founder could be subject to penalties if Facebook doesn't comply with the agreement.
-
Lawmakers in the Senate and House are questioning lobbyists and officials from Facebook, Google, Amazon and Apple on an array of issues, including whether they're so big they stifle competition.
-
Immigration and Customs Enforcement officials scanned driver's license databases and used facial recognition technology to analyze millions of photos without permission in at least three states.
-
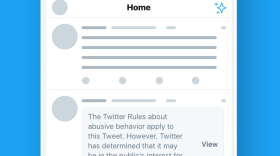
Twitter won't delete the tweets of politicians that are bullying or derogatory, but it will label them. The service has been criticized for its handling of tweets posted by President Trump and others.